Now that AWS has made Windows Server 2016 is available on EC2, you may be thinking about beginning to use it in your cloud deployments.
Here’s a quick tip for EC2 users who do not want their users to be able to create new or use existing Microsoft accounts. You can use policies to prevent users from creating and/or logging into Windows Server with Microsoft accounts. The Active Directory policy, when applied to the default domain policy, will also prevent local logins with Microsoft accounts. This can reduce Windows cloud architects’ concerns about exfiltration of local machine info and, presumably, reduce the telemetry Microsoft receives from both Windows Server 2016 instances that are either domain-joined or which come from local Windows domain members.
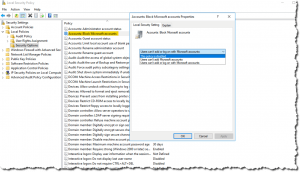
The screenshot nearby shows a non-domain-joined EC2 Windows Server 2016 instance. You can access this policy via secpol.msc.
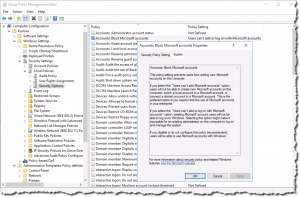
For Active Directory users, there’s an equivalent group policy that can be configured in the GP management console, shown in this screenshot:
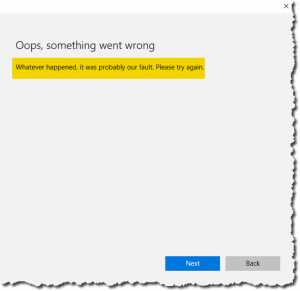
Update 2017-03-20: If you implement the no-Microsoft-account policy as described above and a user attempts to add a Microsoft account to a domain-joined machine where the policy is applied, he or she will receive the unhelpful error below (in this case, from Windows 10 Pro 1607). I wish Microsoft would fix this — it’s not someone’s “fault”. It’s the domain policy working as it should.
Leave a Reply