In January, 2015, this site went 100% “SSL” (or, more accurately, TLS) for a number of reasons, among them the fact that Google SEO has become increasingly dependent on running a secure site.
Running a secure site is something you shouldn’t just use. It’s something you should understand. With Let’s Encrypt, it’s easier than ever before. But you might still want to understand the technology behind Let’s Encrypt.
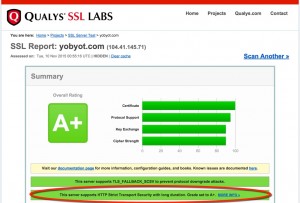
“Thinking Aloud’s” initial conversion to all-TLS went well. But I wanted to know why SSL Labs’s tough test only gave me an A when I tested the site, not an A+. Turns out I’d gone pretty far in securing visits to this blog — but not far enough. Today, I managed to get over the last hurdle, as you can see nearby. I now have the coveted A+ from SSL Labs.
The secret to getting the best grade possible was to implement HTTP Strict Transport Security (or HSTS). When HSTS is on, the Apache web server sends a header to the browser that, in effect, says, “Browser, don’t ever attempt to connect to me using anything other than a secure connection. I mean it: talk to me over secure connections only.” Contained in this header is a time limit. In my case, I set it to 15768000 seconds which is six months. Every time your browser connects to yobyot.com, that header is reset for another six months. Bottom line: your browser is never going to accept a non-secured connection to this blog.
That means is that if for some reason, someone were to try to man-in-the-middle communications between your browser and my Apache server running in the Azure cloud, they won’t be able to. Only I have the certificate for yobyot.com and so, when you visit here, you are assured of getting the unadulterated Alex without anyone snooping or watching you partake of your guilty pleasures. (Sheesh, that’s over the top, eh?)
The beauty of HSTS is, once your browser sees the header, the loop is closed between the server and the browser. I had been offering TLS connections, but not making browsers demand them. With HSTS, I am making your browser “commit” to using only an authenticated, encrypted session. Both sides now know they must use only secure connections.
HSTS is surprisingly easy to implement. If you’ve already implemented TLS, you only need to:
- Make sure
mod-headersis enabled - Add a header directive to your Apache TLS virtual host configuration file (often,
/etc/httpd/conf/ssl.conf)
Here’s an example:
Header always set Strict-Transport-Security "max-age=15768000"
Once you’ve set Apache up to use HSTS, you can verify that the header is being sent to the browser by using any of a number of browser extensions to view the headers. Here I am using HTTP Live Headers in Chrome (click the image to enlarge).
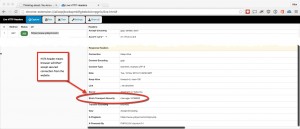
Much better security — and HSTS is easy to implement.
Leave a Reply